External Vulnerability Scans: Safeguarding SME Compliance
- Gary Sinnott

- Dec 19, 2025
- 7 min read

Most British businesses underestimate just how exposed their online systems can be. With cyber attacks on UK companies rising by more than 80 percent in the past year, understanding your external vulnerabilities is not just smart, it is necessary. This guide explains how external vulnerability scans work, why they matter for British organisations, and what steps help protect your company’s digital assets from sophisticated threats.
Table of Contents
Key Takeaways
Point | Details |
Importance of External Scans | External vulnerability scanning is crucial for identifying weaknesses in an organisation’s digital infrastructure before they can be exploited by cyber criminals. |
Balanced Scanning Strategy | Combining external scans with credentialed scans ensures a comprehensive security approach that covers both perimeter weaknesses and internal vulnerabilities. |
Regular Scheduling | Conducting external scans quarterly and after significant network changes enhances ongoing security readiness and compliance with cybersecurity standards. |
Awareness of Limitations | Understanding the inherent limitations of external scans, such as their snapshot nature, is key to developing a robust and dynamic security posture. |
Defining External Vulnerability Scans in Cyber Security
External vulnerability scanning represents a critical security assessment technique that examines an organisation’s digital infrastructure from an outside perspective, mimicking potential cyber attacker approaches. These technical evaluations systematically probe internet-facing systems to identify potential weaknesses that malicious actors could exploit.
At its core, an external vulnerability scan focuses on detecting potential entry points across an organisation’s network perimeter. Managed vulnerability scanning is a fundamental component of security testing designed to uncover existing or emerging vulnerabilities and system misconfigurations. The scan specifically targets external-facing IP addresses, investigating potential weaknesses such as:
Open network ports
Application-level security gaps
Weak authentication credentials for protocols including:
SMTP
POP3
HTTP
VPN services
By comprehensively mapping these potential security risks, businesses can proactively address vulnerabilities before they become potential breach points. External vulnerability scans assess security from an internet-based viewpoint, essentially simulating the reconnaissance techniques used by cyber criminals to identify systemic weaknesses.
Pro Tip: Conduct external vulnerability scans quarterly and immediately after any significant network changes to maintain robust cyber security posture.
Types of Vulnerability Scans and Their Differences
Vulnerability scanning represents a multi-faceted approach to cyber security, with different techniques designed to uncover specific types of system weaknesses. Small and medium enterprises (SMEs) must understand these varied scanning methodologies to build comprehensive security strategies that protect their digital infrastructure effectively.
Network scanning involves investigating an organisation’s entire network infrastructure to identify potential security gaps. This comprehensive approach examines critical network components, including:
Open network ports
Active network services
Security configurations of networking hardware like:
Firewalls
Network switches
Router configurations
Another sophisticated scanning technique is the credentialed vulnerability scan, which provides deeper insights into system vulnerabilities. A credentialed scan allows penetration testers to access systems using login credentials, effectively simulating an insider’s perspective. This method reveals nuanced vulnerabilities that external scans might miss, such as:
Configuration misconfigurations
Outdated software installations
Missing security patches
Internal system weaknesses
The primary difference between external and credentialed scans lies in their approach and depth of investigation. While external scans assess vulnerabilities from an outside perspective, credentialed scans provide a more comprehensive, user-level examination of potential security risks.
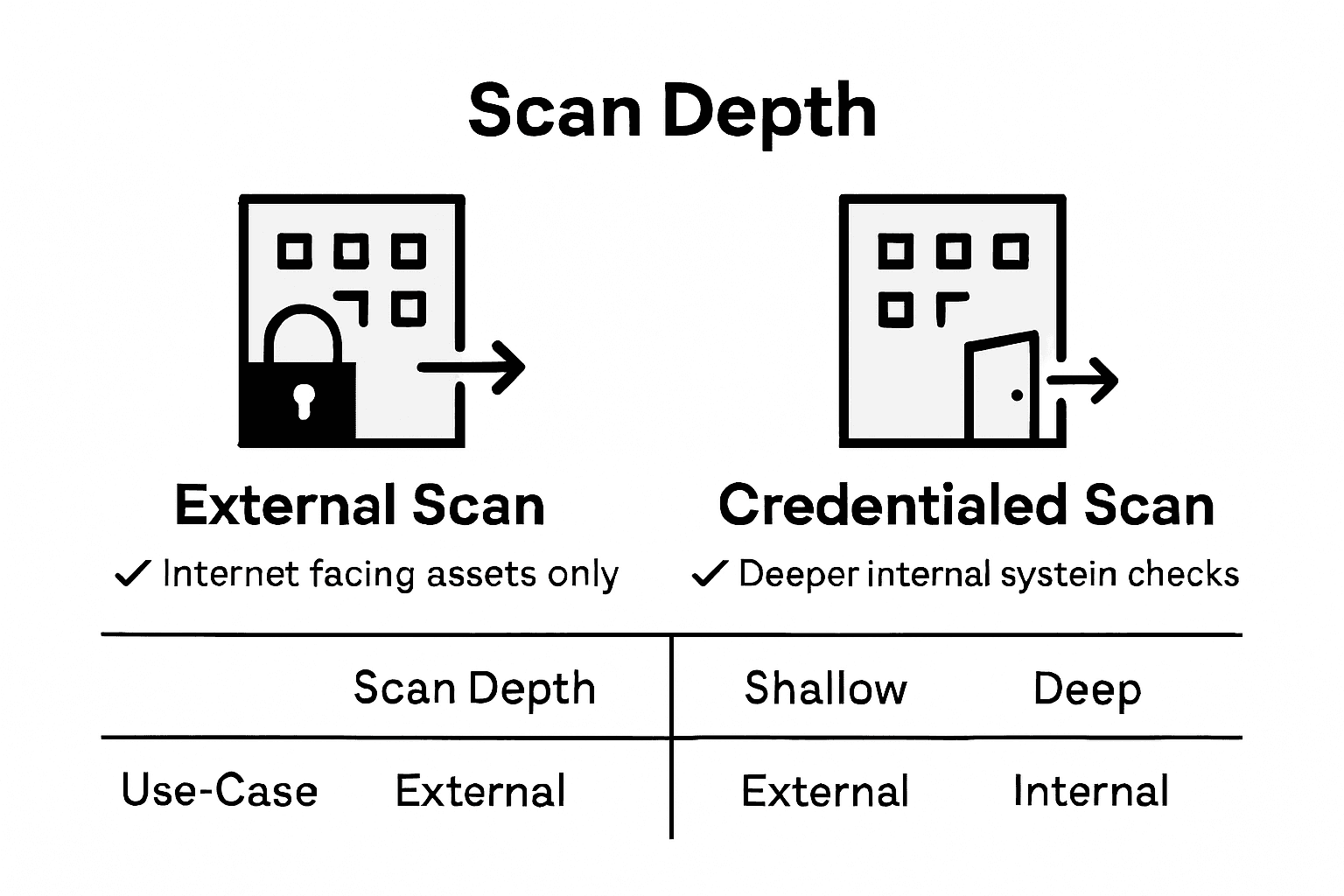
Pro Tip: Implement a balanced vulnerability scanning strategy that combines both external and credentialed scans to ensure comprehensive security coverage.
Here is a comparison of key vulnerability scan types and their main characteristics:
Scan Type | Assessment Depth | Typical Use Case | Security Insights Provided |
External Scan | Surface-level, perimeter | Defending against internet threats | Reveals public-facing weaknesses |
Credentialed Scan | In-depth, internal | Detecting user-level exposures | Identifies hidden system flaws |
Network Infrastructure | Broad, device-focused | Reviewing entire network devices | Spots open ports, misconfigurations |
How External Scans Work for UK Businesses
External vulnerability scanning represents a critical defensive strategy for businesses seeking to protect their digital infrastructure from potential cyber threats. By systematically examining internet-facing systems, organisations can proactively identify and address security weaknesses before malicious actors can exploit them.
External vulnerability assessments are designed to significantly reduce the risk of external breaches through comprehensive scanning techniques. These assessments typically involve a sophisticated process that includes:
Mapping all externally accessible network endpoints
Identifying potential entry points and security vulnerabilities
Analysing network configurations
Detecting unpatched software or misconfigured systems
Checking for weak authentication mechanisms
The scanning process utilises advanced technologies to find vulnerabilities in external-facing services before potential attackers can discover them. This proactive approach allows businesses to make informed decisions about their digital infrastructure, addressing potential security gaps before they become critical risks.

For UK businesses, these external scans are particularly crucial in meeting compliance requirements and demonstrating robust cybersecurity practices. The scans provide a comprehensive view of an organisation’s external security posture, helping to identify potential weaknesses that could compromise sensitive business data or customer information.
Pro Tip: Schedule external vulnerability scans quarterly and immediately following any significant network changes or infrastructure updates to maintain continuous security readiness.
Role in Cyber Essentials and Ongoing Compliance
External vulnerability scans play a pivotal role in achieving and maintaining cyber security certifications, serving as a critical mechanism for demonstrating an organisation’s commitment to robust digital protection. These systematic assessments are not merely a one-time checkbox but a continuous process of identifying, understanding, and addressing potential security vulnerabilities.
PCI DSS Requirement 11.3.2.1 mandates quarterly external vulnerability scans performed by an Approved Scanning Vendor, highlighting the structured approach required for maintaining compliance. These scans are essential for businesses across various sectors, particularly those handling sensitive financial or customer data.
For Cyber Essentials certification, external vulnerability scans are a fundamental requirement. They demonstrate an organisation’s proactive approach to identifying potential security weaknesses across internet-facing systems. Vulnerability management best practices recommend performing internal and external scans at least once per quarter, depending on the complexity of your security environment and frequency of network changes.
The scanning process goes beyond mere compliance, providing businesses with a comprehensive view of their digital security posture. By regularly conducting these assessments, organisations can:
Identify potential security gaps
Prioritise remediation efforts
Demonstrate due diligence to clients and stakeholders
Maintain an up-to-date understanding of their cyber security landscape
Pro Tip: Create a structured vulnerability management calendar that aligns with certification requirements, scheduling scans quarterly and immediately after significant network infrastructure changes.
Risks, Limitations, and Common Pitfalls
External vulnerability scanning, while essential for cyber security, is not an infallible solution. Small and medium enterprises must understand the inherent limitations and potential risks associated with these assessments to develop a comprehensive security strategy.
Defining the precise scope of vulnerability scanning requires careful consideration of multiple critical factors. These factors include determining key parameters such as:
Proposed scanning date and frequency
Scan type: internal versus external
Authentication approach: authenticated or unauthenticated
Focus area: infrastructure or application-specific scanning
Common pitfalls in vulnerability scanning often stem from oversimplified or inconsistent approaches. Many organisations mistakenly view these scans as a one-time compliance exercise rather than an ongoing, dynamic process of security assessment. This misconception can lead to several critical risks:
Incomplete vulnerability detection
Outdated security snapshots
False sense of security
Overlooking emerging threat vectors
Inadequate remediation strategies
Moreover, external vulnerability scans have inherent technical limitations. They provide a snapshot of potential vulnerabilities at a specific moment, which means new risks can emerge between scanning intervals. Automated scanning tools, while sophisticated, cannot fully replicate the nuanced, creative approaches of human threat actors.
The following table summarises common limitations of external vulnerability scans and their business implications:
Limitation | Business Impact | Recommended Mitigation |
Snapshots can miss new threats | Undetected vulnerabilities after scans | Increase scan frequency and monitoring |
Cannot mimic human creativity | Some attacks go unnoticed | Combine with expert penetration testing |
May lead to false sense of security | Potential complacency | Promote ongoing security awareness |
Pro Tip: Implement a multi-layered vulnerability management approach that combines automated external scans with periodic manual penetration testing and continuous monitoring.
Strengthen Your SME’s Cyber Security with Expert Vulnerability Management
External vulnerability scans are vital for protecting your business from evolving cyber threats and meeting compliance requirements such as Cyber Essentials and PCI DSS. Many SMEs struggle with keeping up-to-date scans, managing remediation, and maintaining continuous security without constant stress. This article highlights key challenges including insufficient scan frequency, incomplete vulnerability coverage, and the risk of complacency.
At Freshcyber, we understand these pain points. Our comprehensive Vulnerability Management services help you stay ahead by not only performing thorough external scans but also guiding you through continuous monitoring and remediation. We support busy business owners and IT teams in navigating the complexities of compliance and security. Explore how we tailor solutions specifically for small and medium enterprises facing similar hurdles detailed in the article through our dedicated SME Security resources.

Don’t leave your cyber security and compliance to chance. Take action now by partnering with Freshcyber to automate your vulnerability management and secure lasting peace of mind. Visit Freshcyber to discover how you can simplify compliance and protect your digital infrastructure effectively today.
Frequently Asked Questions
What is an external vulnerability scan?
An external vulnerability scan is a security assessment that evaluates an organisation’s internet-facing systems for potential weaknesses that could be exploited by cyber attackers. It identifies issues like open ports and weak authentication credentials.
How often should I conduct external vulnerability scans for my organisation?
It is recommended to conduct external vulnerability scans at least quarterly and immediately after any significant network changes to ensure continuous security readiness.
What is the difference between external and credentialed vulnerability scans?
External scans evaluate vulnerabilities from an outside perspective, while credentialed scans provide deeper insights by simulating access as an insider user, revealing more nuanced vulnerabilities.
Why are external vulnerability scans important for compliance?
External vulnerability scans are critical for maintaining compliance with security standards, such as Cyber Essentials and PCI DSS, as they demonstrate an organisation’s commitment to identifying and mitigating potential security weaknesses.
Recommended
Comments