Cyber Security Terminology Explained – Key Terms for UK SMEs
- Gary Sinnott

- Dec 21, 2025
- 7 min read

Most British small businesses underestimate just how quickly cyber threats can develop, with over 40 percent of UK firms reporting a security breach last year. Staying informed goes far beyond installing antivirus software and hoping for the best. Mastering core cyber security terminology is crucial for every British organisation that wants to defend its assets and maintain customer trust. This guide breaks down key concepts so your team can spot real risks before criminals strike.
Table of Contents
Key Takeaways
Point | Details |
Understand Core Terminology | Familiarise yourself with essential cyber security terms like malware, ransomware, and phishing. |
Recognise Evolving Threats | Stay informed about common attack methods and incorporate regular training to enhance employee awareness. |
Acknowledge Security Roles | Clearly define key security roles within your organisation to promote effective cyber defence systems. |
Prioritise Compliance and Certification | Ensure your team understands vital compliance terms and certifications to meet legal standards and build trust. |
Core Cyber Security Terms Defined
Navigating the world of cyber security requires understanding key terminology. Fortunately, the National Cyber Security Centre (NCSC) provides comprehensive definitions that help demystify complex technical language. These foundational terms serve as building blocks for understanding digital protection strategies.
Some fundamental cyber security terms every UK small business should know include malware, which represents any software intentionally designed to cause damage to a computer system, network, or user. Ransomware represents a specific type of malicious software that encrypts an organisation’s data and demands payment for its release. Phishing refers to fraudulent attempts to obtain sensitive information by disguising communications as trustworthy sources, often through deceptive emails or websites.
Additional critical terms encompass two-factor authentication (2FA), a security process requiring two different identification methods to verify a user’s identity, and firewall, a network security system that monitors and controls incoming and outgoing network traffic. Cyber security experts recommend understanding these core concepts to build robust digital defence mechanisms for your business.
Pro Tip for SMEs: Regularly update your team’s understanding of cyber security terminology through monthly briefings or training sessions, ensuring everyone speaks the same technical language and recognises potential digital threats.
Recognising Threats and Attack Methods
Cyber threats are constantly evolving, presenting significant challenges for UK small businesses. Understanding the landscape of potential attack methods is crucial for developing robust digital defence strategies. Security vulnerability assessments reveal that SMEs face multiple types of digital risks that require proactive management and strategic planning.

Common attack methods include phishing, where malicious actors send deceptive emails designed to trick employees into revealing sensitive information or clicking dangerous links. Social engineering represents another sophisticated technique where cybercriminals manipulate human psychology to breach security systems. Ransomware attacks have become increasingly prevalent, with criminals encrypting company data and demanding financial payment for its release, potentially causing substantial operational disruption.
Technical attack vectors like distributed denial of service (DDoS) attacks, malware injection, and network intrusion pose significant threats to organisational digital infrastructure. These methods exploit system vulnerabilities, often targeting outdated software, weak password protocols, or unpatched security gaps. Small businesses must remain vigilant, continuously updating their technological defences and training staff to recognise potential security risks.
Here is a quick reference comparing common cyber attack methods and their business impacts:
Attack Method | Typical Target | Potential Business Impact |
Phishing | Employee email users | Data theft, credential compromise |
Ransomware | Company file systems | Data loss, operational disruption |
DDoS | Public web services | Service downtime, reputational harm |
Social Engineering | Individuals/staff | Unauthorised access, fraud |
Malware Injection | Network endpoints | System damage, persistent threats |
Network Intrusion | IT infrastructure | Confidential information exposure |
Pro Tip for SMEs: Implement regular cybersecurity awareness training sessions that simulate real-world attack scenarios, helping employees develop practical skills in recognising and responding to potential digital threats before they escalate.
Understanding Security Roles and Functions
Effective cybersecurity requires a comprehensive understanding of various roles and functions within an organisation’s digital defence strategy. UK Government Security Groups emphasise the critical importance of collaborative threat modelling as a fundamental approach to identifying and mitigating potential security vulnerabilities.
Key security roles include the Chief Information Security Officer (CISO), who provides strategic leadership and oversees the entire security programme, and the Security Analyst, responsible for monitoring systems, investigating potential breaches, and implementing defensive measures. Penetration Testers play a crucial role in proactively identifying system weaknesses by simulating cyberattacks, while Incident Response Specialists develop and execute plans to manage and recover from security breaches.
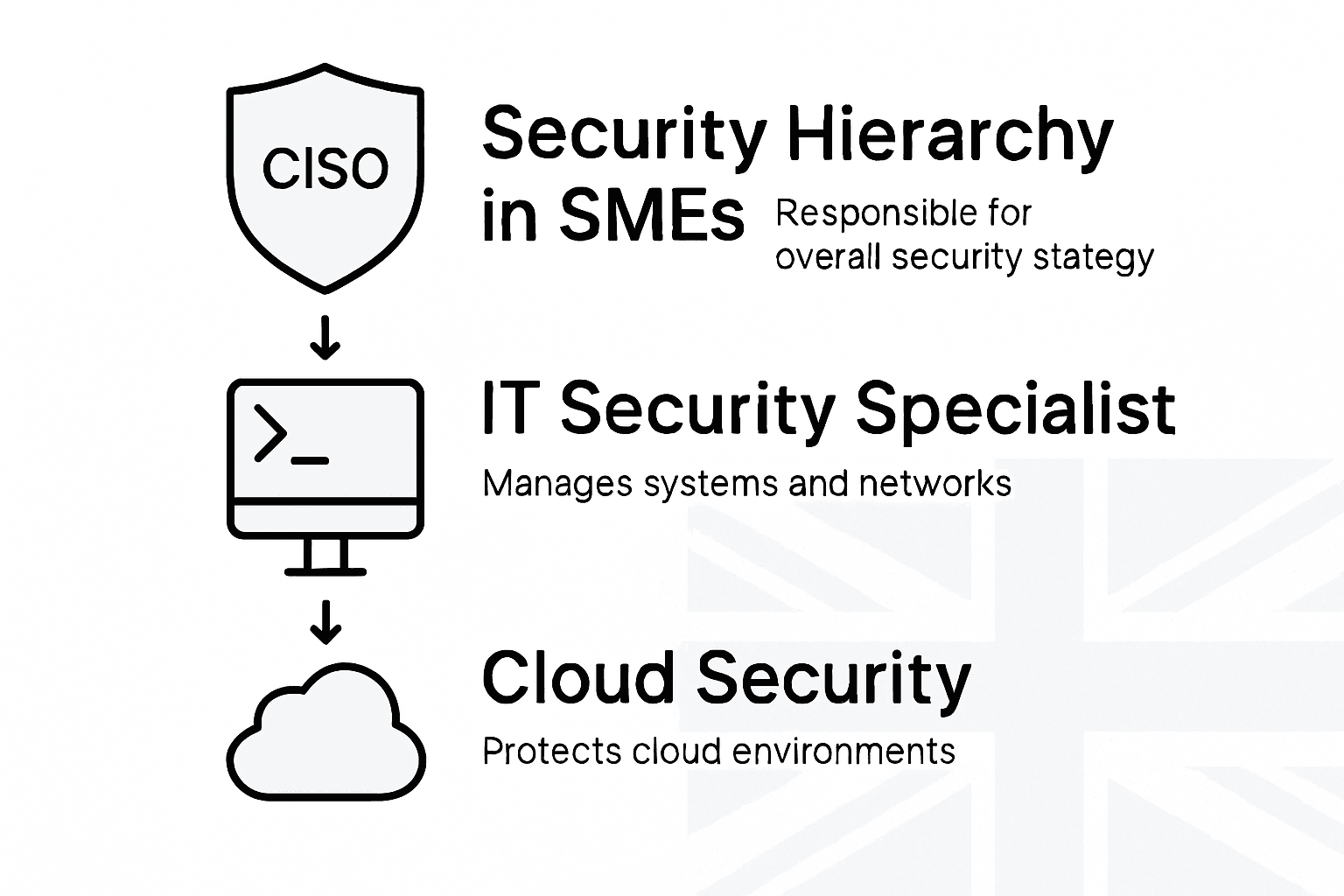
Technical security functions encompass various specialised areas such as network security, application security, and cloud security. These roles involve complex methodologies like threat modelling techniques such as STRIDE and DREAD, which help security professionals systematically categorise, assess, and prioritise potential security risks. Small businesses must understand these roles to build a comprehensive and robust cybersecurity strategy that protects their digital assets and maintains operational resilience.
Pro Tip for SMEs: Consider implementing a rotating security awareness programme that allows team members to learn about different cybersecurity roles and functions, fostering a culture of collective digital responsibility and continuous learning.
Compliance, Certification, and Legal Vocabulary
Comprehensive data security glossaries reveal the complex landscape of legal and regulatory terminology that UK small businesses must navigate. Understanding these critical definitions is essential for maintaining robust cybersecurity practices and ensuring organisational compliance with evolving digital regulations.
Key compliance terminology includes General Data Protection Regulation (GDPR), which governs how organisations handle personal data, and Personally Identifiable Information (PII), referring to any data that could potentially identify a specific individual. Data governance represents the overall management of data availability, usability, integrity, and security within an organisation. Cybersecurity definitions from legal primers emphasise the distinction between various types of digital threats, including cyber attacks and organised cybercrime.
Critical certification standards like Cyber Essentials, ISO 27001, and IASME Governance provide frameworks for businesses to demonstrate their commitment to robust security practices. These certifications require organisations to implement specific security controls, conduct regular risk assessments, and maintain comprehensive documentation of their cybersecurity strategies. Small businesses must understand these standards as they often serve as key requirements for winning contracts and building trust with potential clients.
Below is a summary of leading cyber security certifications and their significance for UK SMEs:
Certification | Focus Area | Business Benefit |
Cyber Essentials | Basic controls, UK focus | Demonstrates baseline compliance |
ISO 27001 | Information management | International credibility, risk reduction |
IASME Governance | SME risk management | Tailored guidance, client assurance |
GDPR Compliance | Data protection laws | Legal adherence, customer trust |
Pro Tip for SMEs: Develop a comprehensive compliance vocabulary cheat sheet for your team, ensuring everyone understands the critical legal and technical terms that impact your organisation’s cybersecurity strategy.
Common Pitfalls and Misunderstood Terms
Cybersecurity education modules highlight critical misunderstandings that frequently expose small businesses to unnecessary digital risks. Many organisations mistakenly believe that basic antivirus software provides comprehensive protection, overlooking the complex landscape of modern cyber threats and the nuanced approaches required for genuine digital resilience.
One significant misconception is the notion of security through obscurity, where businesses assume their small size or perceived low profile protects them from cyberattacks. In reality, cybercriminals often target smaller organisations precisely because they typically have weaker security infrastructure. Another common misunderstanding involves password complexity, with many businesses believing that simple password rotation is sufficient, rather than implementing robust multi-factor authentication and comprehensive password management strategies.
Technical terminology often creates additional confusion, with terms like zero-day vulnerability, social engineering, and lateral movement being widely misunderstood. These concepts represent sophisticated attack methods that go far beyond simple malware infections, requiring advanced understanding and proactive defence mechanisms. Small businesses frequently underestimate the potential impact of these technical vulnerabilities, assuming that standard security measures provide complete protection against increasingly sophisticated digital threats.
Pro Tip for SMEs: Conduct quarterly cybersecurity literacy sessions that demystify technical terminology and challenge existing misconceptions, transforming your team’s understanding from reactive protection to proactive digital resilience.
Master Cyber Security Terminology to Strengthen Your UK SME’s Defences
Understanding cyber security terminology is essential for UK SMEs wanting to build resilient digital defences and avoid costly mistakes like falling victim to phishing or ransomware attacks. If you feel overwhelmed by complex terms such as “risk management” or “penetration testing” this is a common challenge many businesses face when seeking true cyber resilience beyond basic protections. At Freshcyber, we specialise in guiding SMEs through these critical concepts and transforming them into practical, actionable strategies.

Take control of your cybersecurity journey with Freshcyber’s Virtual CISO service. We act as your dedicated security partner, leading you through comprehensive vulnerability management, compliance frameworks like Cyber Essentials and ISO 27001, and tailored risk registers that prioritise your organisation’s unique threats. Don’t wait for an attack to expose gaps in your knowledge or protections. Visit Freshcyber now to start building a robust security foundation informed by clarity and expertise.
Frequently Asked Questions
What is malware and how does it affect my business?
Malware is any software specifically designed to cause damage to a computer system, network, or user. It can lead to data loss, theft of sensitive information, and operational disruptions for businesses.
How can phishing attacks impact my organisation?
Phishing attacks involve fraudulent emails or communications that trick employees into revealing confidential information or accessing malicious links. This can result in data breaches and significant financial losses.
What are the benefits of implementing two-factor authentication (2FA)?
Two-factor authentication adds an extra layer of security by requiring users to verify their identity using two different methods. This significantly reduces the risk of unauthorised access, even if a password is compromised.
Why is understanding cybersecurity compliance important for small businesses?
Understanding cybersecurity compliance, such as GDPR and data governance, is vital for small businesses to ensure they handle personal data lawfully. Compliance also helps build trust with clients and reduces the risk of legal repercussions.
Recommended
Comments